Scenario:
For this lab you need REAL hardware. You can’t use switches in GNS3!
You need at least a Cisco Catalyst 3560 switch for this lab.
Your are the senior network engineer of a small company specialized in switching solutions. The datacenter houses a couple of servers and you would like to increase security. You prefer to keep all servers within the same subnet and prevent the usage of access-lists. It sounds like Private VLANs could help you out…
Goal:
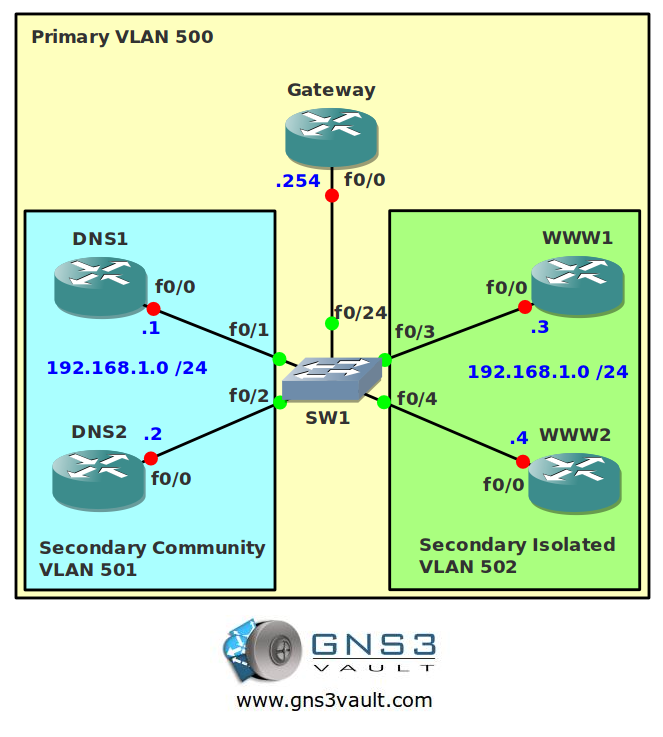
- Configure all IP addresses as specified in the topology picture.
- Configure VLAN 500 to be the primary VLAN.
- Configure VLAN 501 as a secondary community VLAN.
- Configure VLAN 502 as a secondary isolated VLAN.
- Configure the correct mapping between the primary and secondary VLANs.
- Configure DNS1 and DNS2 to be in the secondary community VLAN 501.
- Configure WWW1 and WWW2 to be in the secondary isolated VLAN 502.
- Configure fa0/24 on SwitchA as the promiscious port.
- DNS1 and DNS2 should be able to communicate with each other and the Gateway.
- WWW1 and WWW2 should only be able to communicate with the Gateway.
It took me 1000s of hours reading books and doing labs, making mistakes over and over again until I mastered all the switch protocols for CCNP.
Would you like to be a master of switching too? In a short time without having to read 900 page books or google the answers to your questions and browsing through forums?
I collected all my knowledge and created a single ebook for you that has everything you need to know to become a master of switching.
You will learn all the secrets about VLANs, Private VLANs, primary/secondary VLANs and more.
Does this sound interesting to you? Take a look here and let me show you how to Master CCNP SWITCH
IOS:
Basic IOS for the switch should be sufficient. No special features needed.
Topology:
Video Solution:
Configuration Files
You need to register to download the GNS3 topology file. (Registration is free!)Once you are logged in you will find the configuration files right here.

The How to Master series helps you to understand complex topics like spanning-tree, VLANs, trunks, OSPF, EIGRP, BGP and more.
Written by René Molenaar - CCIE #41726


excellent
thank you 🙂
Cant find any vedio.. please help.
Video isn’t here yet, I’ll be uploading them this week.
Hi Rene could you please tell me the IOS and the router required in Gns3 for this lab.I tried using 3640 & 3660 image but the Switch did not allow the command (config-vlan)# private-vlan.Thanks 🙂
Hi,
There’s no way to do this on a router or in GNS3. You need a real switch for this lab…a 3560 or a 3750. No way to emulate this 🙂
Rene
Very nice, thanks Rene.
Thanks!
great job
i downloaded the topology but it dosent work.help plz
These are only the config files. You’ll need a real 3560 switch to do this lab.
enter your message here…
Hi
thank you ,but I’d like to know which format do you use in Topology.
because , I download it when I opened it doesn’t show .
thank you in advance
Jack
Thanks ur video!!!
Good lab, Rene, not too hard…
Also in the books is the private-vlan trunk feature. Is this tested on the exam, or just something to keep in mind?
Dear Rene,
I have configured the private vlan but on issuing #show vlan private-vlan type.. the type column shown NON-OPERATIONAL and the primary and secondary column shown NORMAL. Please how do I solve this problem.
Thanks
Let’s see your configuration.
This is my partial configuration and on issuing the show vlan private-vlan type command, the TYPE COLUMN shows non-operational. I am using IOU on GNS3 Early version v1.0.
SW (config)# vtp mode transparent
SW (config)# vlan 100
SW (config-vlan)# private-vlan community
SW (config-vlan)#exit
SW (config)#vlan 200
SW (config-vlan)#private-vlan isolated
SW (config-vlan)#exit
SW (config)#vlan 500
SW (config-vlan)#private-vlan primary
SW (config-vlan)# private-vlan association 100,200
SW (config-vlan)#end
The same problem is faced by me while using IOU on GNS3 Early version 1.0 Beta 3. Have you found the solution.
Hi…I am not able to download the topology…can anyone help?
There is only one file, the final configuration for the switch. You can’t do this in GNS3…you’ll need a Cisco Catalyst 3560 or 3750 switch for this.
Can I use 3550 cisco switch for this topology?
I’m afraid not, you will need a 3560 at least.
I guess to properly do this lab, the only way is at least a 3560 switch and at least 1 route rand 4 hosts or 5 routers.
My problem is that I’m trying to do my own scenario with my personal topology, and I can’t make a port a private-vlan promiscuous port without turning off its trunking, which borks up my ability to communicate with the gateway for testing.
Hi Rene,
Please help as I am trying to understand what kind of layer 3 traffic are process, since Isolated vlan hosts only talk to Promiscuous port and hosts within a community vlan (do not talk to hosts in other community vlan) but can talk to each other and Promiscuous port. I can’t see where inter-vlan routing is required here?
From what I read, to allow Layer 3 processing of private VLAN ingress traffic, VLAN interface of a primary VLAN. Isolated and community VLANs secondary VLANs can be mapped to the L3 interface (VLAN network interface of a primary VLAN).