Scenario:
As the owner of a small company you notice some of your employees are slacking off at the job and spending their time at Facebook, Twitter and some other sites. You want to configure your network so these sites are blocked. While you are at it you also want to block some of the worms that are on the Internet.
Goal:
- All IP addresses have been preconfigured for you.
- OSPF has been preconfigure for full connectivity.
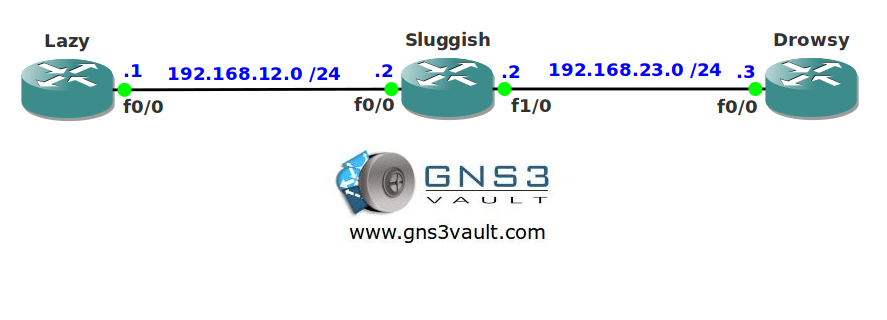
- Configure router Sluggish so all traffic from Twitter is dropped on the FastEthernet 1/0 interface.
- Configure router Sluggish so it can detect the NIMDA worm and drops the traffic on the FastEthernet 1/0 interface.
- Configure router Sluggish so it marks Youtube traffic down to DSCP 0 on the FastEthernet 1/0 interface.
IOS:
c3640-jk9s-mz.124-16.bin
Topology:
Video Solution:
Configuration Files
You need to register to download the GNS3 topology file. (Registration is free!)Once you are logged in you will find the configuration files right here.

Do you want your CCNA or CCNP Certificate?
The How to Master series helps you to understand complex topics like spanning-tree, VLANs, trunks, OSPF, EIGRP, BGP and more.
Written by René Molenaar - CCIE #41726


Create class maps that match on protocol http url, set the appropriate policy maps to drop or set the dscp value and then nest the policy maps.
Can’t edit my post, may also want to enable ip nbar protocol discovery on the interfaces
Hi Steve,
That’s how to do it 🙂 The Cisco website has an example of how to use NBAR to detect worms:
http://www.cisco.com/en/US/products/sw/iosswrel/ps1835/products_tech_note09186a0080110d17.shtml
Rene
idea, just enabling the ip nbar protocol discovery on the interface and creat class- map ospf and apply drop on this class under the policy map , you will find the ospf in loading state not full state 🙂
[quote]dea, just enabling the ip nbar protocol discovery on the interface and creat class- map ospf and apply drop on this class under the policy map , you will find the ospf in loading state not full state[/quote]
That’ll work but that’s a "very" quick and dirty method of getting the job done 😛 Better to keep the OSPF adjacency up and running and filter using another method 😉
when you going to come out QOS book Rene
Works like charm. Thanks a lot.
Hi ReneMolenaar,
Does this work for me :
class-map match-all YOUTUBE
match protocol http [color=red]mime[/color] “*youtube*”
class-map match-all TWITTER
match protocol http mime “twitter”
Thank you
http://www.cisco.com/c/en/us/support/docs/ios-nx-os-software/ios-software-releases-122-mainline/4615-nimda.html
After looking at a cisco page for blocking NIMDA, I configed this:
Sluggish#sho run | s class-map
class-map match-any YOUTUBE
match protocol http url “*youtube*”
class-map match-any NIMDA
match protocol http url “*readme.eml*”
match protocol http url “*.ida*”
match protocol http url “*cmd.exe*”
match protocol http url “*root.exe*”
class-map match-any TWITTER
match protocol http url “*twitter*”
Sluggish#
Sluggish#sho run | s policy-map
policy-map INBOUND
class YOUTUBE
set precedence 1
class TWITTER
drop
class NIMDA
drop
Sluggish#
Sluggish#sho run int fa1/0
Building configuration…
Current configuration : 127 bytes
!
interface FastEthernet1/0
ip address 192.168.23.2 255.255.255.0
duplex auto
speed auto
service-policy input INBOUND
end
Sluggish#sho policy-map int fa1/0
FastEthernet1/0
Service-policy input: INBOUND
Class-map: YOUTUBE (match-any)
0 packets, 0 bytes
5 minute offered rate 0 bps, drop rate 0 bps
Match: protocol http url “*youtube*”
0 packets, 0 bytes
5 minute rate 0 bps
QoS Set
precedence 1
Packets marked 0
Class-map: TWITTER (match-any)
0 packets, 0 bytes
5 minute offered rate 0 bps, drop rate 0 bps
Match: protocol http url “*twitter*”
0 packets, 0 bytes
5 minute rate 0 bps
drop
Class-map: NIMDA (match-any)
0 packets, 0 bytes
5 minute offered rate 0 bps, drop rate 0 bps
Match: protocol http url “*readme.eml*”
0 packets, 0 bytes
5 minute rate 0 bps
Match: protocol http url “*.ida*”
0 packets, 0 bytes
5 minute rate 0 bps
Match: protocol http url “*cmd.exe*”
0 packets, 0 bytes
5 minute rate 0 bps
Match: protocol http url “*root.exe*”
0 packets, 0 bytes
5 minute rate 0 bps
drop
Class-map: class-default (match-any)
8 packets, 752 bytes
5 minute offered rate 0 bps, drop rate 0 bps
Match: any