Scenario:
A host on your network has been surfing the web and transfers files far too much. Your boss is old school and does not like class-based QoS nor MQC. You have to find a way to police traffic from that host before it cripples your network!
Goal:
- Nothing has been preconfigured for you!
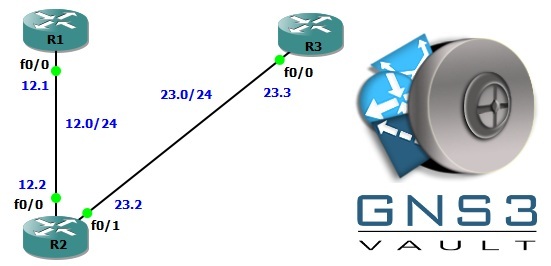
- Make the proper physical connections as outlined in the diagram.
- The bandwidth between R1 and R2 is 496 kbps. Configure this.
- Add a static default route onto both R1 and R3 as they represent hosts.
- Ensure you have IP connectivity from R1 to R3 before continuing.
- Without using MQC or CB Policing, police traffic from R1, configured on R2 as follows. Bc should be equal to the CIRs:
- Police all traffic to 496 kbps, dropping all exceeding traffic. Before this traffic is forwarded, apply the additional policing …
- Police web traffic at 400 kbps, dropping all exceeding traffic.
- Police FTP traffic at 160 kbps, dropping all exceeding traffic.
- Police ICMP traffic at 200 kbps, dropping all exceeding traffic.
IOS:
c3725-adventerprisek9-mz.124-7.image
Topology:

Do you want your CCNA or CCNP Certificate?
The How to Master series helps you to understand complex topics like spanning-tree, VLANs, trunks, OSPF, EIGRP, BGP and more.
Written by René Molenaar - CCIE #41726


Thank you..After completing the LAB how do I test it ?
In order to solve this lab without using MQC and Class-based QoS (still wondering why anyone will do that:) ) I’ve used a combination of interface rate-limit subcommand in combination with extended access-list, find below part of my configuration on R2,
Rate-limit config:
interface FastEthernet0/0
bandwidth 496
ip address 192.168.12.2 255.255.255.0
rate-limit input access-group 100 496000 496000 496000 conform-action continue exceed-action drop
rate-limit input access-group 101 400000 400000 400000 conform-action continue exceed-action drop
rate-limit input access-group 102 160000 160000 160000 conform-action continue exceed-action drop
rate-limit input access-group 103 200000 200000 200000 conform-action continue exceed-action drop
rate-limit output access-group 100 496000 496000 496000 conform-action continue exceed-action drop
rate-limit output access-group 101 400000 400000 400000 conform-action continue exceed-action drop
rate-limit output access-group 102 160000 160000 160000 conform-action continue exceed-action drop
rate-limit output access-group 103 200000 200000 200000 conform-action continue exceed-action drop
Access-list config:
access-list 100 permit ip any any
access-list 101 permit tcp any any eq www
access-list 102 permit tcp any any range ftp-data ftp
access-list 103 permit icmp any any
I was only able to test the ICMP portion by pinging from R1 to R3 with a 15000 byte size repeated 100 times, then observing the show interface rate-limit ( you can filter it down with | sec access-list 103).
It works but I don’t know if that was the intended solution, so I’m also looking forward for the video solution.
Thank.
Thanks for the start up idea.
I was thinking if Generic Traffic Shaping could be used as an alternative.
http://www.cisco.com/c/en/us/td/docs/ios/12_2/qos/configuration/guide/fqos_c/qcfgts.html#wp1000916
when will be available video with solutions?
I would appreciate if a video were made. Thank you
thank you!!!
Hi Rene,
I don’t have any prior knowledge of QoS. Can you please tell me what should be the starting point to learn this topic.
Thank you
Taslim
The basic MQC constructs is a good starting point, along with DSCP values.
R2#sh run int fa0/1
Building configuration…
Current configuration : 480 bytes
!
interface FastEthernet0/1
ip address 192.168.23.2 255.255.255.0
rate-limit output access-group 101 400000 400000 400000 conform-action transmit exceed-action drop
rate-limit output access-group 102 160000 160000 160000 conform-action transmit exceed-action drop
rate-limit output access-group 103 200000 200000 200000 conform-action transmit exceed-action drop
rate-limit output 496000 496000 496000 conform-action transmit exceed-action drop
duplex auto
speed auto
end
R2#sh run | i access-list
access-list 101 permit tcp any any eq www
access-list 102 permit tcp any any eq ftp
access-list 103 permit icmp any any
Verification for icmp packet:
R2#sh int rate-limit | s 103
matches: access-group 103
params: 200000 bps, 200000 limit, 200000 extended limit
conformed 2134 packets, 1266712 bytes; action: transmit
exceeded 38 packets, 56296 bytes; action: drop
last packet: 904ms ago, current burst: 199076 bytes
last cleared 00:14:17 ago, conformed 11000 bps, exceeded 0 bps
My config is as follows:
R2#sho run | s access-l
access-list 100 permit tcp any any eq www
access-list 100 permit tcp any any eq 443
access-list 110 permit tcp any any eq ftp
access-list 120 permit icmp any any
R2#sho run int fa0/0
Building configuration…
Current configuration : 485 bytes
!
interface FastEthernet0/0
bandwidth 496
ip address 12.12.12.2 255.255.255.0
rate-limit output access-group 100 400000 50000 50000 conform-action transmit exceed-action drop
rate-limit output access-group 110 400000 50000 50000 conform-action transmit exceed-action drop
rate-limit output access-group 120 200000 25000 25000 conform-action transmit exceed-action drop
rate-limit output 496000 62000 62000 conform-action transmit exceed-action drop
duplex auto
speed auto
end
R2#sho int fa0/0 rate-limit
FastEthernet0/0
Output
matches: access-group 100
params: 400000 bps, 50000 limit, 50000 extended limit
conformed 0 packets, 0 bytes; action: transmit
exceeded 0 packets, 0 bytes; action: drop
last packet: 1939428ms ago, current burst: 0 bytes
last cleared 00:03:37 ago, conformed 0 bps, exceeded 0 bps
matches: access-group 110
params: 400000 bps, 50000 limit, 50000 extended limit
conformed 0 packets, 0 bytes; action: transmit
exceeded 0 packets, 0 bytes; action: drop
last packet: 1939436ms ago, current burst: 0 bytes
last cleared 00:03:37 ago, conformed 0 bps, exceeded 0 bps
matches: access-group 120
params: 200000 bps, 25000 limit, 25000 extended limit
conformed 1594 packets, 2232860 bytes; action: transmit
exceeded 317 packets, 478702 bytes; action: drop
last packet: 88284ms ago, current burst: 24226 bytes
last cleared 00:03:36 ago, conformed 82000 bps, exceeded 17000 bps
matches: all traffic
params: 496000 bps, 62000 limit, 62000 extended limit
conformed 7 packets, 504 bytes; action: transmit
exceeded 0 packets, 0 bytes; action: drop
last packet: 33264ms ago, current burst: 0 bytes
last cleared 00:04:04 ago, conformed 0 bps, exceeded 0 bps
don’t forget the burst values are in bytes and the rate-limit (police) value is in bits. You have to device your burst in kbs by 8 in order to convert bits to byte values.