Scenario:
You are a big poker fan and also a master in networking. Your favorite online poker room has been experiencing connection problems and you decided to help them out. They added another link to the service provider for extra redundancy, now the only thing left to do is making sure the BGP configuration is also correct…can you go all-in on this one?
Goal:
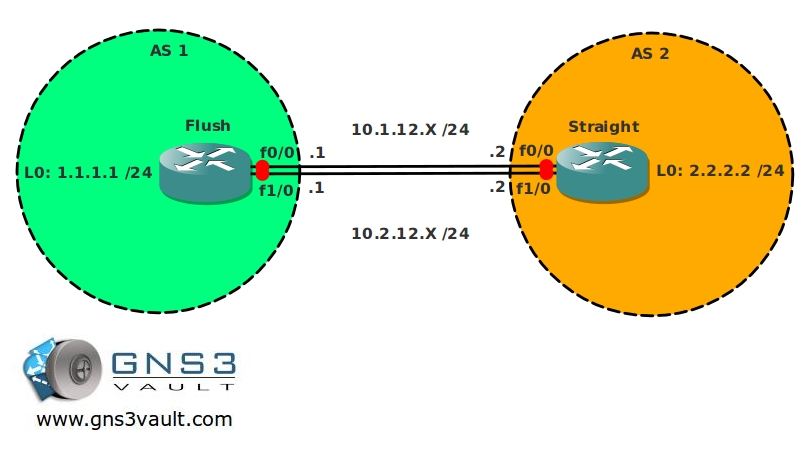
- All IP addresses have been preconfigured as specified in the topology picture.
- Create 2 static routes pointing to each others loopback interface:
For the 10.1.12.X link use an administrative distance of 10.
For the 10.2.12.X link use an administrative distance of 20. - Ensure you can ping every IP address.
- Configure EBGP and use the correct AS numbers, the updates must be sources from the loopback interfaces.
- You are not allowed to use EBGP Multihop to solve this problem.
IOS:
c3640-jk9s-mz.124-16.bin
Topology:
Video Solution:
Configuration Files
You need to register to download the GNS3 topology file. (Registration is free!)Once you are logged in you will find the configuration files right here.

Do you want your CCNA or CCNP Certificate?
The How to Master series helps you to understand complex topics like spanning-tree, VLANs, trunks, OSPF, EIGRP, BGP and more.
Written by René Molenaar - CCIE #41726


To get more challenge in this lab add the following requirement:
– You are not allowed to use disable-connected-check command
There is one more choice to do this!
Cool! to be honest I’m not sure which method you are referring to…;D Will have to think a bit about that.
link to the video has gone dead did you know ? video is still on youtube though..
I think he has to talking about ttl-security command it similar to mutlihop but subtracts the hop count i.e 255-N ? and expects no less.
Thanks for the comment about the Youtube video, just fixed it.
ttl-security should work I think.
Thanks for the video and for the LAB
if it isn’t ebgp multihop, nor is it disable-connected-check, it probably is ttl-security feature.
It seems any combination of ebgp-multihop / ttl-security hops / disable-connected-check will work for this case and both sides don’t have to have the same configuration.
So, how exactly does the disable-connected-check affect the TTL count? It’s a good lab, and it all works, but I’m looking for a quick explanation on what this command does behind the scenes.