Scenario:
This morning you woke up in a cell feeling dizzy and nauseous, it appears you were kidnapped by a mixture of agents from federal agencies. Your task is to finish this security test, if you pass you might end up becoming their next security agent…with blurry eyes you start your task!
Goal:
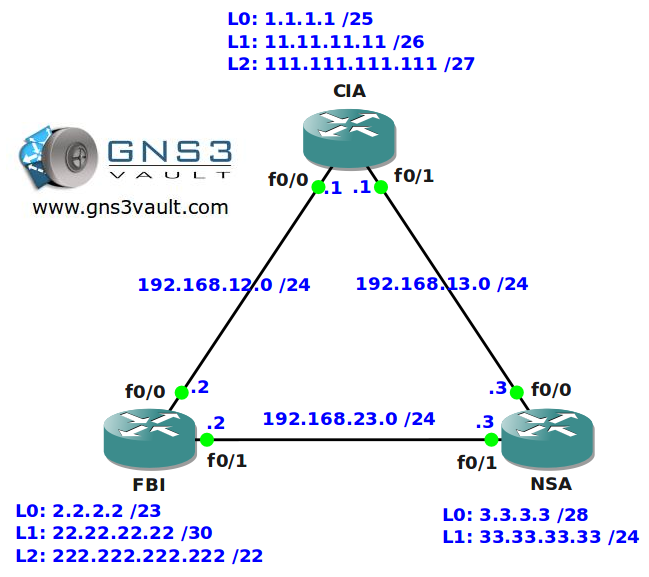
- All IP addresses have been configured for you, look at the topology picture for the IP addresses.
- OSPF has been configured for full connectivity.
- Make sure you use the most specific wildcard for all your access-lists.
- You are only allowed to use standard access-lists.
- Configure your network so traffic from router CIA’s L0 interface can’t reach any networks on router FBI.
- Extend the access-list you just created to include router CIA’s L1 and L2 interface.
- Configure your network so traffic from router FBI’s L0 and L1 interface are unable to reach any networks on router NSA.
Topology:
Video Solution:
Configuration Files
You need to register to download the GNS3 topology file. (Registration is free!)Once you are logged in you will find the configuration files right here.

Do you want your CCNA or CCNP Certificate?
The How to Master series helps you to understand complex topics like spanning-tree, VLANs, trunks, OSPF, EIGRP, BGP and more.
Written by René Molenaar - CCIE #41726


In final config NSA
access-list 2 deny 2.2.0.0 0.0.254.255
Why do you have 0.0.254.255 for your wildcard mask?
access-list 2 deny 2.2.0.0 0.0.254.255
I thought for /23, you would use the following?
255.255.255.255 – 255.255.254.0 = wildmask
NSA(config)#access-list 5 deny 2.2.2.0 0.0.1.255
NSA(config)#access-list 5 deny 2.2.0.0 0.0.1.255
I think best and most effective wildcard mask for 2.2.2.2/23
NSA(config)#access-list 5 deny 2.2.2.0 0.0.1.255
ip address – 2.2.2.2/23
mask – 255.255.254.0
Subnet ID – 2.2.2.0
Broadcast IP – 2.2.3.255
You are totally right! It should be:
access-list 2 deny 2.2.0.0 0.0.254.255
Just did it on top of my head and made a mistake while recording the video (*shame on me*)!
Rene
I went to do this lab and no configs for IP address or OSPF are on the routers. Can you provide the pre configs so I dont have to do this?
I just checked the configs, all routers have a startup-config that has IP addresses and OSPF pre-configured.
Did you check if GNS3 is using the configs or just opening the topology.net file?
Thanks you, muchas gracias from Perú.
Hi Rene,
For 2.2.2.2/23 the wildcard mask isn’t it 0.0.1.255?
Great work by the way:)
Thanks!
hey everyone
why do you use wildcard mask 0.0.0.127 in router FBI to deny access from int loop0?
why don’t you use 0.0.0.0?
im waiting for your answer,
thank you very much
it is done as the subnet mask, which is specified in the lab
if you do 0.0.0.0 mean only 1 ip address v’ll be allowed
Which loopback0 interface do you mean? From which router?
A wildcard is a reverse subnet mask. You take the subnet mask, write it down in binary and change the 0 to 1 and vice versa. Calculate it back into decimal and you have a wildcard.
to me it seems like the wildcard mask should be 0.0.1.255
For which interface?
I build everything from scratch for more practice. I learn better that way 🙂 but thanks alot for the premade CFG’s. Anyway,
Can anyone kindly explain the wildcard mask situation on all these routers? I thought like others here that it would also be 0.0.1.255 for L0 on FBI router 2.2.2.2/23. ?
on FBI router i applied ACL inbound like this :
Standard IP access list DENY_LOOPBACKs_from_CIA
10 deny 1.1.1.0, wildcard bits 0.0.0.127 log (5 matches)
20 deny 11.11.11.0, wildcard bits 0.0.0.63 (11 matches)
30 deny 111.111.111.0, wildcard bits 0.0.0.31
40 permit any log (55 matches)
This is the ACL i applied for NSA router
Standard IP access list DENY_LOOPBACKS_FROM_FBI
10 deny 2.2.2.0, wildcard bits 0.0.0.255 log
20 deny 22.22.22.20, wildcard bits 0.0.0.3 log (5 matches)
30 permit any (107 matches)
I got everything working the way I wanted to. However I know I may not have used the best and most effective wildcard mask.
What could I had done differently or better next time?
Thanks so much everyone.
Go CISCO !!
am trying repeatedly to advertise loopback 2 of CIA router and L1 of FBI but only in vain. it is not shown in route table to other routers. they are not learning route 111.111.111.0/27 and 22.22.22.22/30 not sure why. i tried many things like disbaling the interfacing and configuring again. i have mentioned ip ospf point-to-point in every loopback. am able to ping these 2 loopbacks from respective routers but not from other 2 router.
advertised as network 111.111.111.0 0.0.0.31 area 0
network 22.22.22.0 0.0.0.3 area 0
Thanx for the site! Its GREAT!!!
Hi Rene,
These are Awesome labs and really helpful.
I have a query.
When you mention ‘traffic from L0 interface cant reach’ that should mean the single IP has to be blocked not whole subnet.
correct me if I am wrong.
Hello! Have you valid ios for GNS3? I have different ios and any time any lab i need find ios
i have configure this on NSA router to block FBI traffic of Lo 0 and Lo 1
Standard IP access list 2
10 deny 2.2.2.0, wildcard bits 0.0.1.255
20 deny 22.22.22.0, wildcard bits 0.0.0.3
30 permit any (22 matches)
but ping goes successfull
rene plz tell me why u use 111.111.111.96…….
Could you please tell me what the name of the IOS image is?
Thanks you, muchas gracias from Perú.