Scenario:
After configuring standard and extended access-lists for the agents of three well-known agencies you were promoted to junior security operator. It’s now time to upgrade your skills and show them how to implement named access-lists.
Goal:
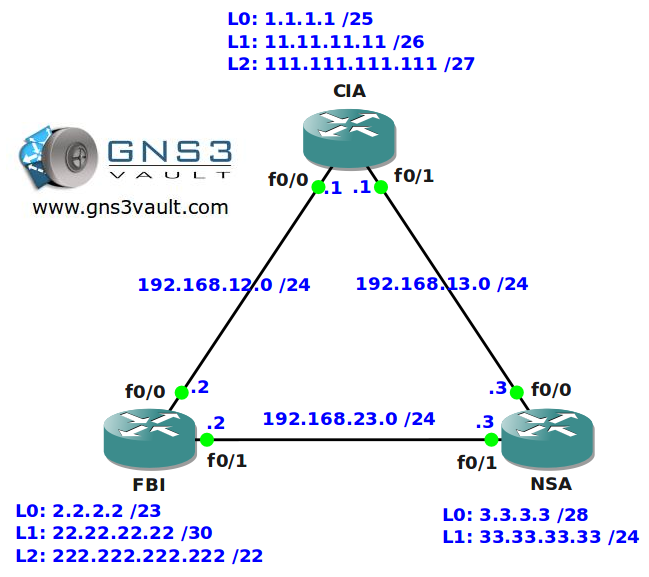
- All IP addresses have been configured for you, look at the topology picture for the IP addresses.
- OSPF has been configured for full connectivity.
- All routers are running services like HTTP, HTTPS, TELNET and SSH.
- Make sure you use the most specific wildcard for all your access-lists.
- You are not allowed to use numbered access-lists, only named access-lists.
- Configure the network so users from router NSA’s L1 interface are not allowed to reach the HTTPS server on router CIA’s L2 interface.
- Configure the network so nobody is allowed to reach HTTP servers on router NSA except the L2 interface on router FBI.
- Configure the network so users from router NSA’s L0 interface are allowed to reach the HTTPS server on router CIA’s L2 interface.
- Configure the network so users from router CIA’s L2 interface are not allowed to SSH into router FBI’s 222.222.222.222 IP address.
Topology:
Video Solution:
Configuration Files
You need to register to download the GNS3 topology file. (Registration is free!)Once you are logged in you will find the configuration files right here.

Do you want your CCNA or CCNP Certificate?
The How to Master series helps you to understand complex topics like spanning-tree, VLANs, trunks, OSPF, EIGRP, BGP and more.
Written by René Molenaar - CCIE #41726


[quote]Configure the network so nobody is allowed to reach HTTP servers on router NSA except the L2 interface on router FBI.[/quote]
I think it will be more correct, if I understand correctly the condition.
Extended IP access list ALLOWFBI
10 permit tcp 222.222.220.0 0.0.3.255 any eq www
20 deny tcp any any eq www
30 permit ip any any
Although I could be wrong..
This is also what i came up with. Thought i was wrong but glad to see others have it the same way too 🙂
[quote]think it will be more correct, if I understand correctly the condition.
Extended IP access list ALLOWFBI
10 permit tcp 222.222.220.0 0.0.3.255 any eq www
20 deny tcp any any eq www
30 permit ip any any
Although I could be wrong..[/quote]
That is a good looking access-list.
I have been attempting to apply the ACL DENYNSA :
[quote]10 deny tcp 33.33.33.0 0.0.0.255 111.111.111.96 0.0.0.31 eq 443
20 permit ip any any[/quote]
to fa0/0-1:
[quote]ip access-group DENYNSA out[/quote]
But no traffic hits DENYNSA (my counters never change).
Is this because “By default, locally-generated packets are not inspected by outgoing access-lists?” (See: [url=http://blog.ine.com/2008/02/13/tricks-with-local-policy-routing/]Tricks with Local Policy Routing[/url])
Hi Rene,
For the following task
"Configure the network so nobody is allowed to reach HTTP servers on router NSA except the L2 interface on router FBI."
If we apply this access list on the video, we also block the http traffic passing through this router. For instance think about the link bettween FBI and CLI has gone and FBI try to reach a web server on CIA trough NSA. In this situation, FBI uses its outgoing interface ip as source ip and match with deny any any statement at the bottom of the list.
My advice is for such situations to apply access-list with "ip http access-class" statement. In this way, we can avoid not to block transit traffic through the router.
What do you think about my comments?
HI. What is the difference between:
1. 11 permit tcp host 111.111.111.111 eq 443 host 3.3.3.3
2. 11 permit tcp host 111.111.111.111 host 3.3.3.3 eq 443
I wrote it the second way and it doesnt work. Why is that?
Thanks.