Scenario:
You work for a local copyshop in a small town in the USA. To improve network security you have installed a new Intrusion Detection System (IDS) but right now it’s only receiving traffic from router Ditto. You are familiar with SPAN for switches but you don’t know how to export traffic on routers…let’s see if there’s a copycat in you!
Goals:
- All IP addresses have been preconfigure for you.
- EIGRP has been configured for connectivity.
- Configure router Ditto so all EIGRP and HTTP traffic is exported to router IDS.
IOS:
c3640-jk9s-mz.124-16.bin
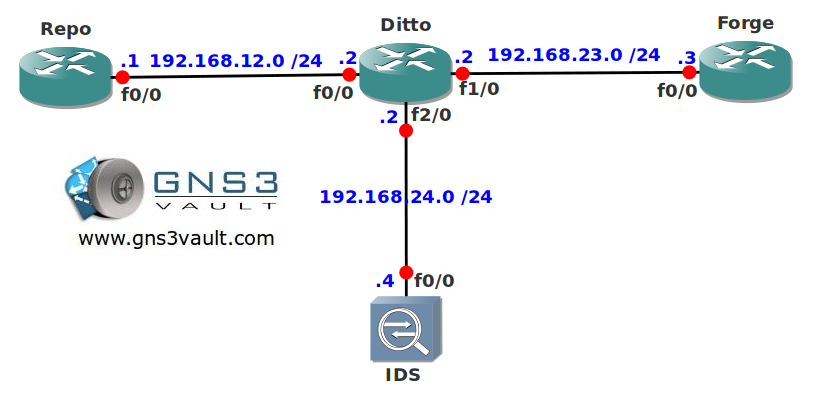
Topology:
Video Solution:
Configuration Files
You need to register to download the GNS3 topology file. (Registration is free!)Once you are logged in you will find the configuration files right here.

Do you want your CCNA or CCNP Certificate?
The How to Master series helps you to understand complex topics like spanning-tree, VLANs, trunks, OSPF, EIGRP, BGP and more.
Written by René Molenaar - CCIE #41726


Hi Rene,
Thank you for the lab explanation.
In the traffic-export profile for MAC-address destination you have configured the router Ditto f2/0 mac-address. Shouldn’t it be the MAC-address of the IDS sensor, as it is described here:
http://www.cisco.com/en/US/docs/ios/12_3t/12_3t4/feature/guide/gt_rawip.html
Thanks again for your labs.
Hey, Rene
Great lab!!!
Thanks so much for all your help. Your labs have been amazing.
I just have one small question about this lab. In your lab solution, you defined the access-list called "INSPECT."
But, when you added the access-list in the traffic-export profile, you called it "EXPORT."
Should it not be the same access list ?
Even when you do "show ip traffic-export" on Ditto at the end, it says "Access List EXPORT [Unknown]." When I run that command, it says "Access List 100 [Extended]."
Thanks again for all the helpful labs.
Regards
This looks like one of my monday morning jobs 😉 This is the correct config:
[code]ip access-list extended INSPECT
permit eigrp any any
permit tcp any any eq www
ip traffic-export profile IDS
interface FastEthernet2/0
bidirectional
incoming access-list INSPECT
outgoing access-list INSPECT
mac-address
interface FastEthernet0/0
ip traffic-export apply IDS
interface FastEthernet1/0
ip traffic-export apply IDS[/code]
Cheers for that ….