Scenario:
As part of the security team you are always looking for ways to improve security within the company. You heard bad things about fragmented IP packets being a security risk to your network. You decide to block them using an access-list.
Goal:
- All IP addresses have been configured for you, look at the topology picture for the IP addresses.
- OSPF has been preconfigured for you.
- Configure router Mirror so IP fragments from network 1.1.1.0 /24 are not allowed to reach router Flash.
Topology:
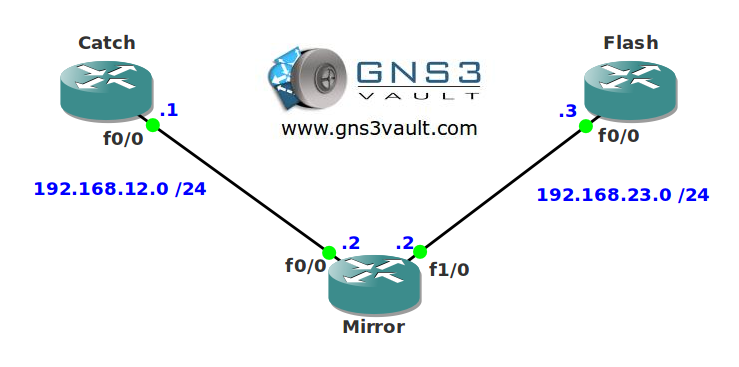
Video Solution:
Configuration Files
You need to register to download the GNS3 topology file. (Registration is free!)Once you are logged in you will find the configuration files right here.

Do you want your CCNA or CCNP Certificate?
The How to Master series helps you to understand complex topics like spanning-tree, VLANs, trunks, OSPF, EIGRP, BGP and more.
Written by René Molenaar - CCIE #41726


I achieved fragmentation by sending ICMP packets with large Datagrams.
R1#ping
Protocol [ip]:
Target IP address: 3.3.3.3
Repeat count [5]:
Datagram size [100]: 15000
Timeout in seconds [2]:
Extended commands [n]:
Sweep range of sizes [n]:
Type escape sequence to abort.
Sending 5, 15000-byte ICMP Echos to 3.3.3.3, timeout is 2 seconds:
…..
Success rate is 0 percent (0/5)
R2#sh ip access-lists
Extended IP access list 100
10 deny ip any any fragments ([b]122 matches[/b])
20 permit ip any any (39 matches)