Scenario:
As part of the security team you are always looking for ways to improve security within the company. Recently you are being plagued by different sources sending spoofed IP packets. You want to protect your network by checking for the source IP addresses using Unicast Reverse Path Forwarding. Let’s see if you can find the root of this one…
Goal:
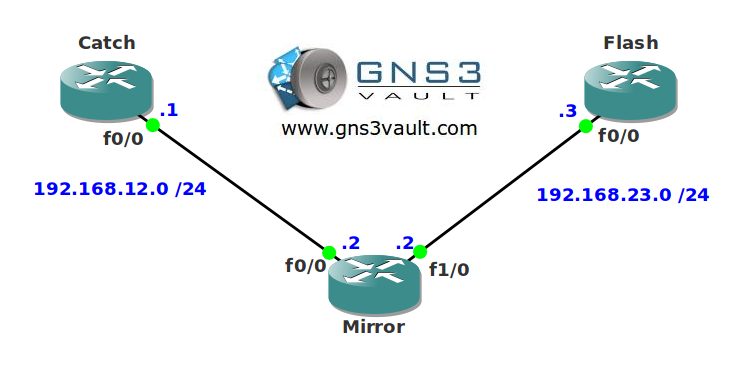
- All IP addresses have been configured for you, look at the topology picture for the IP addresses.
- OSPF has been preconfigured for you.
- Configure router Mirror so traffic on the FastEthernet 1/0 interface will be dropped if the source IP address doesn’t match the next hop address that router Mirror has in its routing table.
- Configure router Mirror so traffic on the FastEthernet 0/0 interface will be dropped it the source IP address doesn’t match anything that router Mirror has in its routing table.
- Configure router Mirror so all dropped packets are logged.
Topology:
Video Solution:
Configuration Files
You need to register to download the GNS3 topology file. (Registration is free!)Once you are logged in you will find the configuration files right here.

Do you want your CCNA or CCNP Certificate?
The How to Master series helps you to understand complex topics like spanning-tree, VLANs, trunks, OSPF, EIGRP, BGP and more.
Written by René Molenaar - CCIE #41726


match the next hop address that router Mirror has in its routing table
ip verify unicast source reachable-via rx 100
match anything that router Mirror has in its routing table.
ip verify unicast source reachable-via any 100
Should the answer not be as above? One is strict and one is loose mode.
Hi
Can I ask question ? according to your example if we ping from the source 11.11.11.11 the packet will drop, right ? but there is no effect if we remove the uRPF command ” ip verify source reachable-via rx 100″ the same result ?? I couldn’t understand that if we ping with this command or without still we will got the same results, in other word it will depend on routing table entry if its from OSPF environment “process” it will pass if not it will dropped? can you explain what or how uRPF command does not change the result ?? you can try by your self just remove the command “ip verify ………” and do the same ping you will see the same results.
Waiting to here your reply ASAP. Thanks a lot.
Zaid